Metaverse Security Best Practices for Entertainment
Protecting Digital Assets in Immersive Environments

Protecting Digital Assets in Immersive Environments
Protecting digital assets in immersive environments, such as virtual and augmented reality, is crucial for maintaining user trust and preventing security breaches. These environments often involve sensitive data, including personal information, financial transactions, and intellectual property. Robust security measures are essential to safeguard this data from unauthorized access, use, disclosure, disruption, modification, or destruction. It's vital to consider the unique characteristics of immersive environments when implementing these security measures.
The nature of immersive experiences often blurs the lines between the physical and digital worlds, creating new avenues for potential attacks. Users may be more vulnerable to social engineering tactics or exploits that leverage the immersive environment itself. Therefore, security protocols need to be adaptable and proactive, anticipating and mitigating these evolving threats.
Implementing Robust Security Measures
Implementing robust security measures in immersive environments requires a multi-layered approach. This includes employing strong encryption protocols to protect data transmitted and stored within the system. Implementing multi-factor authentication (MFA) is crucial to verify user identities and prevent unauthorized access. Furthermore, thorough security audits and penetration testing are vital to identify vulnerabilities and address them before they can be exploited.
Regular updates and patches for software and hardware components are essential to maintain the security posture. This proactive approach helps to mitigate known vulnerabilities and ensures the system remains protected against emerging threats. Constant vigilance and adaptation to new attack vectors are critical to maintaining a robust security framework.
User Awareness and Training
User awareness and training play a significant role in enhancing the overall security posture of immersive environments. Educating users about potential security risks and best practices for safe online behavior is vital. This includes teaching users how to identify phishing attempts and other malicious activities tailored for immersive environments. Providing clear guidelines for data protection and responsible use of the platform is essential to mitigate risks.
Emerging Technologies and Future Trends
The field of immersive technology is constantly evolving, bringing new challenges and opportunities in security. Emerging technologies, such as blockchain and zero-trust security models, offer promising avenues for enhancing security in immersive environments. These technologies can enhance data integrity, transparency, and user authentication, while also supporting the development of novel security frameworks. Future trends in immersive environments will likely involve more intricate security measures to combat increasingly sophisticated attacks.
It's important to stay updated on the latest research and developments in immersive technology security. This will enable organizations to adapt their security strategies to address future threats and maintain a robust defense against emerging cyber-attacks.
Implementing Robust Authentication and Access Control
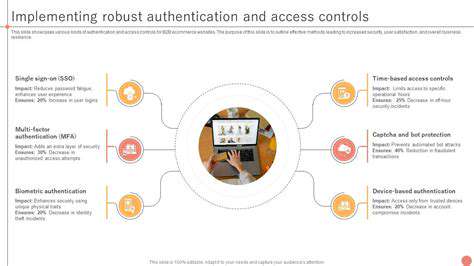
Understanding Authentication Fundamentals
Authentication is a crucial security component in any application or system. It's the process of verifying the identity of a user or entity. This involves establishing trust and ensuring that only authorized individuals or systems can access protected resources. A robust authentication system is paramount for maintaining data integrity and preventing unauthorized access, safeguarding sensitive information and ensuring the overall security posture of the application.
Effective authentication methods employ various techniques to validate user credentials. These methods range from simple password-based systems to more complex multi-factor authentication approaches. A well-designed authentication strategy is essential for establishing a secure foundation for any application.
Choosing the Right Authentication Method
Selecting the appropriate authentication method is critical. Factors such as the sensitivity of the data being protected, the risk tolerance of the organization, and the technical capabilities of the system should all be considered. Different authentication methods offer varying levels of security and complexity, and the optimal choice depends on the specific needs of the application.
Consider the trade-offs between security and usability. A highly secure method might be cumbersome for users, while a user-friendly method could have vulnerabilities. Careful consideration of these factors is essential for selecting a robust and practical authentication solution.
Implementing Multi-Factor Authentication
Multi-factor authentication (MFA) is a powerful technique that enhances security by requiring users to provide multiple forms of identification. This typically involves combining something the user knows (like a password), something the user has (like a security token), or something the user is (like a biometric scan). This layered approach significantly reduces the risk of unauthorized access.
Implementing MFA adds a critical layer of security. It effectively mitigates the risk of password breaches and significantly strengthens the overall security posture of the system. This approach is highly recommended for applications handling sensitive data.
Securing User Credentials
Storing user credentials securely is paramount. Never store passwords in plain text; instead, always use strong hashing algorithms to encrypt them. This protects against data breaches and ensures that even if a database is compromised, the actual passwords remain unreadable.
Implementing robust password policies is essential. These policies should enforce strong password requirements, such as minimum length, complexity, and regular password changes. This ensures that users employ strong passwords and discourages the use of easily guessable or reused credentials.
Handling Authentication Errors
Properly handling authentication errors is vital for a user-friendly and secure experience. Clear and informative error messages should be displayed to users without revealing sensitive information. This helps users understand the reason for the failed authentication attempt and what steps they should take to resolve it.
User-friendly error messages are critical for guiding users. Providing accurate and helpful information reduces frustration and allows users to quickly resolve authentication issues, preventing them from abandoning the application.
Auditing and Monitoring Authentication
Regularly auditing and monitoring authentication attempts is essential for detecting and responding to security threats. This involves tracking login attempts, identifying suspicious activity, and ensuring that all authentication events are logged and reviewed. Maintaining detailed logs provides valuable insights into potential security risks.
Implementing robust logging mechanisms to track authentication activity is critical. This enables proactive threat detection and helps in identifying unusual patterns or malicious attempts to gain access. This proactive approach significantly enhances the overall security posture of the system.
Safeguarding Virtual Assets and Intellectual Property
Protecting Digital Identities
In the metaverse, digital identities are crucial for accessing services and interacting with others. Robust authentication methods, like multi-factor authentication and strong, unique passwords, are paramount. This layered security approach significantly reduces the risk of unauthorized access and the potential for identity theft, which can have far-reaching consequences, especially in a virtual environment where digital assets and reputation are intertwined.
Implementing strong password policies and educating users on the importance of secure password practices within the metaverse is essential. Beyond passwords, exploring advanced biometric authentication methods and zero-knowledge proofs can further enhance security and prevent unauthorized access to virtual identities, protecting users' sensitive information and their virtual presence.
Securing Digital Assets
Virtual assets, including NFTs, virtual land, and in-game items, represent significant financial and personal value within the metaverse. Robust encryption and secure storage solutions are essential to safeguard these assets from theft and unauthorized access. Utilizing blockchain technology with its inherent security features can further enhance the protection of these virtual assets, ensuring their integrity and preventing fraudulent activities.
Implementing secure transaction protocols and auditing mechanisms is crucial to prevent fraudulent activities and ensure the legitimacy of transactions. Establishing clear ownership records and transparent transfer mechanisms are important to protect the rights of asset owners and prevent disputes in the virtual world.
Protecting Intellectual Property
The metaverse presents unique challenges to protecting intellectual property (IP). Digital creations, virtual designs, and unique in-world experiences can easily be copied or misused. Implementing robust digital rights management (DRM) systems and utilizing watermarking technologies can help protect original content and prevent unauthorized replication. This is particularly important for creators who rely on their virtual creations for income or reputation.
Establishing clear legal frameworks and enforcing IP rights within the metaverse is essential. Platforms should actively monitor and address IP infringement to deter malicious actors and support the rights of creators. International collaboration and standardized approaches to IP protection in the metaverse are crucial for fostering a secure and innovative environment.
Mitigating Risks from Malicious Actors
The metaverse environment attracts malicious actors who seek to exploit vulnerabilities and gain unauthorized access to resources. Proactive security measures, including intrusion detection systems and real-time monitoring, are critical for mitigating these risks. Implementing robust threat intelligence systems to identify emerging threats and vulnerabilities is crucial for staying ahead of malicious actors.
Ensuring Privacy and Data Security
User privacy and data security are paramount in the metaverse. Data minimization principles and transparent data handling practices are essential for building trust and ensuring user confidentiality. Implementing strict data encryption protocols and access controls is vital to prevent unauthorized access to personal information. Users should have the ability to control their data and understand how it is being used within the metaverse ecosystem.
Developing user-friendly mechanisms for data subject rights requests and dispute resolution processes is critical to address user concerns and maintain a secure and reliable metaverse environment. Transparency and accountability in data handling practices are essential for building trust and fostering a positive user experience within the virtual world.
Promoting a Secure Metaverse Culture
Establishing Trust and Transparency
A crucial aspect of fostering a secure metaverse culture is establishing a robust system of trust and transparency. This necessitates clear and consistent communication of policies and procedures regarding user data security, privacy, and ethical conduct. Users need to understand how their information is being handled and what protections are in place to safeguard it. Transparency in decision-making processes related to moderation and conflict resolution is also essential to build user confidence and foster a sense of community responsibility.
Implementing transparent reporting mechanisms, allowing users to easily flag inappropriate content or behavior, is vital. This feedback loop is critical for identifying and addressing issues promptly, fostering a safe and respectful environment for everyone. Open communication channels between metaverse platforms and users are essential for addressing concerns and grievances effectively.
Encouraging Responsible User Behavior
Promoting a culture of responsible user behavior is paramount to the long-term security and success of the metaverse. This involves educating users about potential risks, such as online harassment, scams, and misinformation. Comprehensive educational campaigns should explain the importance of privacy settings, strong passwords, and recognizing phishing attempts.
Encouraging users to report any suspicious activity or harmful content they encounter is vital. Clear guidelines on acceptable conduct, coupled with robust reporting mechanisms, are necessary to create a supportive environment where users feel empowered to address problematic behavior.
Promoting empathy and understanding among users is crucial. A strong emphasis on respect and inclusivity can mitigate conflicts and foster a more welcoming and secure environment for everyone, regardless of background or identity. Active community moderation plays a significant role in fostering a positive and safe atmosphere.
Implementing Robust Security Measures
Effective security measures are essential to protect users from malicious actors and ensure the integrity of the metaverse environment. This includes implementing strong encryption protocols to safeguard user data and transactions. Implementing multi-factor authentication and other advanced security measures can significantly reduce the risk of unauthorized access and data breaches.
Continuous monitoring and analysis of user activity and system vulnerabilities are critical to identifying and addressing potential security threats proactively. Regular security audits and vulnerability assessments are necessary to maintain a robust security posture. This proactive approach can mitigate risks and ensure the safety and stability of the metaverse.
Fostering Collaboration and Regulation
Collaboration among metaverse platforms, developers, and regulatory bodies is essential to establish common security standards and best practices. This collaborative approach can ensure a consistent and effective approach to addressing security challenges across different platforms.
The development of clear and comprehensive regulations for the metaverse is necessary to address specific challenges. These regulations should consider issues such as data privacy, intellectual property rights, and the prevention of harmful content. The creation of a clear legal framework is critical to navigating the complexities of the metaverse and ensuring its responsible development.
Read more about Metaverse Security Best Practices for Entertainment
Hot Recommendations
- Immersive Culinary Arts: Exploring Digital Flavors
- The Business of Fan Funded Projects in Entertainment
- Real Time AI Powered Dialogue Generation in Games
- Legal Challenges in User Generated Content Disclaimers
- Fan Fiction to Screenplays: User Driven Adaptation
- The Evolution of User Driven Media into Global Entertainment
- The Ethics of AI in Copyright Protection
- Building Immersive Narratives for Corporate Training
- The Impact of AI on Music Discovery Platforms
- AI for Audience Analytics and Personalized Content