AI's Role in Content Security and Anti Piracy
Enhancing Content Security with Predictive Analytics
Anticipating Digital Piracy Through Data Analysis
Decoding Piracy Patterns
Modern analytics solutions have revolutionized how we approach content protection. Advanced pattern recognition techniques now enable security teams to spot irregularities in content consumption that may indicate piracy activity. Rather than reacting to incidents, organizations can now examine years of download statistics, streaming behaviors, and access patterns to forecast potential threats. This proactive stance fundamentally changes the piracy prevention landscape, allowing content owners to prepare defenses before breaches occur.
Multi-Source Intelligence Gathering
Effective piracy prediction requires tapping into diverse data streams. Security analysts combine information from public forums, social media chatter, and internal platform metrics to create comprehensive threat profiles. Community-generated content often provides early warnings about emerging piracy methods. When cross-referenced with CDN traffic logs and geo-location data, these insights become powerful predictors of illegal distribution networks.
Building Adaptive Prediction Systems
Creating effective monitoring solutions involves balancing technical sophistication with practical usability. Some organizations employ regression models that track piracy probability based on historical patterns, while others implement complex neural networks that learn from each new data point. The most successful implementations combine multiple approaches, using simpler models for broad trend analysis while reserving advanced algorithms for detecting sophisticated attacks.
Strategic Resource Allocation Through Predictive Insights
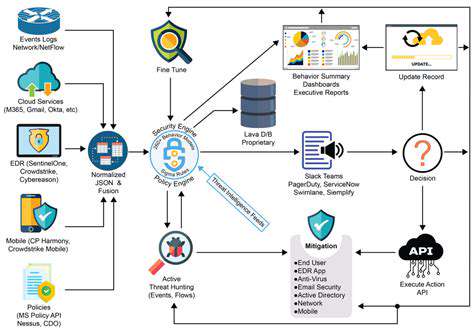
Geographic Threat Mapping
Security teams now use predictive models to generate dynamic piracy heat maps. These visual tools highlight regions showing unusual download spikes or abnormal access patterns, allowing companies to concentrate enforcement efforts where they're needed most. The system accounts for cultural factors, local regulations, and technological infrastructure to provide nuanced risk assessments.
Measuring Defense Effectiveness
Modern analytics don't just identify threats - they quantify how well countermeasures perform. By establishing baseline metrics before implementing new protections, organizations can precisely measure their impact. Some platforms even run simulated attacks to test defense systems, using the results to refine future strategies. This evidence-based approach ensures security investments deliver maximum value.
Anticipating Criminal Innovation
Piracy methods constantly evolve, but predictive systems can spot the early signs of new techniques. When certain content types suddenly appear on unauthorized platforms or when specific technologies gain popularity in hacker forums, these systems flag potential new threats. Security teams use these alerts to develop targeted responses, often staying ahead of would-be pirates.
AI-Powered Content Protection Ecosystem
Intelligent Monitoring Solutions
Contemporary content surveillance systems operate with remarkable efficiency. These platforms automatically scan hundreds of channels simultaneously, using natural language processing to identify potential copyright violations in text, audio, and video formats. Their learning algorithms improve continuously, recognizing new piracy variants faster than human reviewers ever could.
Instantaneous Threat Response
The speed of automated detection creates unprecedented response capabilities. When systems identify unauthorized content distribution, they can initiate takedown procedures within seconds. Some advanced platforms even implement poison pill countermeasures, automatically degrading pirated content quality or embedding tracking markers in suspected leaks.
Competitive Intelligence Applications
Beyond piracy prevention, these analytical tools provide valuable market insights. By monitoring content consumption patterns across legitimate and unauthorized channels, companies gain a comprehensive view of audience preferences. This intelligence informs everything from regional licensing strategies to content development decisions, creating competitive advantages in crowded media markets.
Sentiment-Based Content Optimization
Sophisticated analysis tools now evaluate audience reactions across legal and pirated platforms. By comparing engagement metrics and sentiment trends, content creators can identify what resonates with viewers. This feedback loop helps refine future productions, potentially reducing piracy appeal by better serving legitimate audience demands.

Read more about AI's Role in Content Security and Anti Piracy
Hot Recommendations
- Immersive Culinary Arts: Exploring Digital Flavors
- The Business of Fan Funded Projects in Entertainment
- Real Time AI Powered Dialogue Generation in Games
- Legal Challenges in User Generated Content Disclaimers
- Fan Fiction to Screenplays: User Driven Adaptation
- The Evolution of User Driven Media into Global Entertainment
- The Ethics of AI in Copyright Protection
- Building Immersive Narratives for Corporate Training
- The Impact of AI on Music Discovery Platforms
- AI for Audience Analytics and Personalized Content